The online world delivers instant access to unlimited shopping choices, nearly unlimited information, and global communications. It also offers an unprecedented degree of anonymity. This anonymity can be a blessing, but it also gives bad actors more places to hide as they work to steal information or to profit from scams and fraud.
To solve this problem, many companies have turned to user authentication technologies. Secure authentication is an effective method to protect your customers from stolen accounts and information. But how do you know what authentication method is right for your systems, infrastructure, and network?
2FA vs. MFA
What’s the difference between two-factor authentication (2FA) and multi-factor authentication (MFA)? Multi-factor authentication means using more than one user authentication factor and 2FA means using two different factors. MFA might mean two factors, or it could be more than two. So, 2FA is MFA, just at its most basic level.
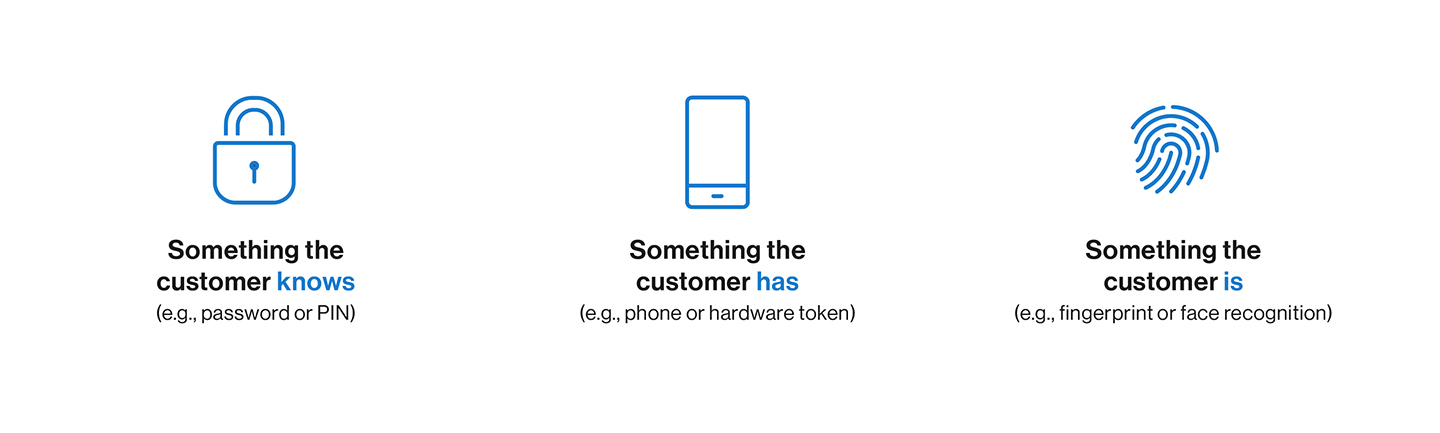
There are three major categories for authentication factors:
- Knowledge or “something the user knows” (password/username or answers to security questions)
- Possession or “something the user has” (hardware token, SMS one time password (OTP), authentication application, etc.)
- Inherence or “something the user is” (biometric authentication including thumbprints, facial scans, etc.)
The most common second factor used today is an SMS one time password (OTP). While SMS has its fair share of criticism in the security world, its popularity is anchored in two key advantages over other forms of a Possession factors:
- First, SMS is nearly ubiquitous across the globe – by implementing SMS 2FA, you can reach nearly all users and add security with just one integration.
- Second, SMS doesn’t require another physical device to be carried – like a hardware token – as the user’s phone is the physical device they have in their possession.
As the leader in SMS 2FA, Telesign is a strong believer in using multiple authentication factors for better platform security. But you’re probably wondering if you need more than two.
Are Three Factors Better?
It’s a natural question to ask. If two factors are good, three must be better, right? The truth is that each authentication type has its strengths and weaknesses. When it comes to the Knowledge factor, emails and passwords offer minimal friction to end users, but this information can easily become leaked and security questions can be guessed.
For Possession, with the widespread prevalence of smartphones, access to SMS passwords is easy, but these devices can be hijacked or phished. Other types of Possession require users to carry a separate physical device that generates a code or a fob to plug in for hardware authentication.
And when it comes to Inherence and biometric authentication, it’s very difficult to steal a thumb print or face scan. But, biometric technology is still expensive, can leave you vulnerable to biometric data breaches, and still has some level of inaccuracy.
As we know, you can’t ever achieve 100% platform protection all the time. It’s simply not possible. Innovative bad actors will always work to find work arounds and flaws. What you can do to prevent unauthorized access, fake accounts, and potential fraud is to layer identity and authentication measures that balance your security needs with user experience and conversion.
2FA Is Not Enough
You might have heard people saying that SMS 2FA is not enough. In fact, you might even have heard that from us. Two-factor authentication only verifies “existence” and “possession” of the phone number– it doesn’t check if the account itself is risky. So, even if you’ve successfully authenticated a user with 2FA, it’s not always enough on its own to prevent account fraud.

2FA does a lot of the authentication heavy lifting, but it can’t protect against everything. Phishing, social engineering attacks, session hacking, man-in-the-middle attacks, and other types of scams are all real threats to your platform security and won’t always be stopped by implementing 2FA.
You might be thinking: “If two factors aren’t enough, should I deploy all three methods of authentication: Possession, Knowledge, and Inherence? “
Maybe, but not necessarily. Adding additional verification measures improves confidence in identity of your user. However, additional factors and more challenges adds more friction to registrations and logins which can negatively affect conversion and user experience.
With all that in mind, the question you should be asking isn’t “what’s the best authentication method?” but instead is “how can I achieve the most platform security without adding too much friction for my end users?”
Layering Platform Security Methods
While SMS 2FA is not enough on its own, one-time SMS passcodes are still very effective at stopping many types of account theft and fraud. The prevalence of SMS makes it the simplest, most cost-effective way to reach the most users with minimum friction. But, will adding an additional factor check or challenge work for you?
Biometrics are certainly emerging as a viable second or third factor of authentication. But, today, they’re still expensive, and not as easy to deploy as other options. Adding additional knowledge challenges, or another possession challenge is an option, but these will also add friction.
When balancing friction with security, the best approach is a risk-based solution. Or, in other words, assessing the risk of the account, phone number, or other identifying information and challenging users for more information or additional authentications only when it shows elevated risk.
Using Digital Identity to Lower Risk
Digital Identity solutions like phone number reputation scoring can help determine individual risk-level for each user and phone number on your platform. With phone number reputation intelligence, multiple behavior signals associated with that number are analyzed to achieve greater accuracy in identifying risky behavior and security threats to your system.
Mobile devices are an ever-present part of our society these days and phone numbers are almost always required for new account registration. By using data inherently tied to the phone numbers that you’re already using, you can immediately understand risk signals that point to SIM Swap Fraud, mis-matched ownership, and more to approve, reject, or challenge the users for more information.
The benefits of layering on risk intelligence and digital identity go beyond just knowing if you should approve a new accountâ Digital Identity solutions like Telesign’s Intelligence and Phone ID can help identify potential SIM swap fraud, account access from suspicious locations, mis-matched account and phone number ownership, and more. These signals help protect you and your users from Account Takeover attacks during password resets, new user registrations, and transaction approvals.
â
More Security, Less Friction
Digital Identity solutions, like phone reputation intelligence, all happen instantaneously and invisibly to your users. As a result, they don’t introduce needless friction to the account registration or login process, making for a better user experience.

Deploying mandatory authentication methods to keep your customers safe will improve your certainty with the identity of your users. It goes without saying that MFA is a requirement to conduct business in today’s online world. SMS 2FA is still a great option for its accessibility and cost. Adding a Digital Identity solution to help you measure risk and help guide further challenges is a more seamless solution than mandatory third factor authentication and offers a better overall user experience by keeping friction low.
The Takeaway
To recap:
- SMS OTP is still the most popular form of MFA today, but alone it is not enough
- Three authentication methods are technically more secure, but adds significant, often unnecessary friction.
- Added security factors help security but can harm conversion and user experience with added friction, so new verification factors should be added judiciously.
- Biometric authentication comes with its own weaknesses and cannot protect you against some of the biggest gaps in two-factor authentication, and bad actors will continue to innovate so long as fraud is profitable.
- Digital Identity solutions like phone number reputation intelligence can make your online platform more secure and can verify new accounts and alert you to suspicious actions behind the scenes with minimal friction to your end users.
Our recommendation? Stick with SMS 2FA as your primary authentication. But layer it with Digital Identity solutions to help you identify risky users before they ever access your platform.
â