Account takeovers (ATO) are a growing problem for web and mobile app businesses. Personally identifiable information (PII) obtained through data breaches and phishing attacks can be used to gain unauthorized access to consumer accounts.
Port-out fraud is a type of ATO attack that occurs when a mobile telephone number is moved to another provider without authorization. Fraudsters port phone numbers to hijack a mobile phone number and receive authentication codes for financial and other types of important accounts.
In this API series blog post, you’ll learn how to unlock critical ATO risk signals to detect suspicious behavior—like if a phone number has been ported—to proactively protect your customer accounts against fraud.
Detect porting with phone number insights
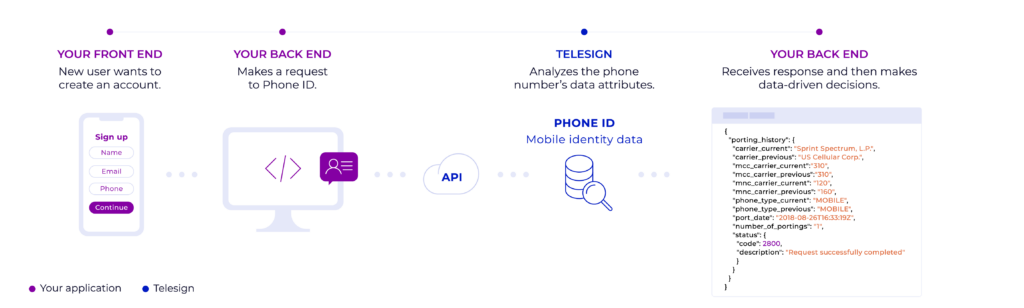
Telesign Phone ID protects your platform by providing real-time information on the device type and contact information associated with a phone number, along with other identity attributes.
The Porting History identity attribute helps you maintain account integrity and detect port-out fraud by providing insights on if an end user’s phone number has been recently ported. If a phone number is ported from one carrier to another, the information you get in a response includes:
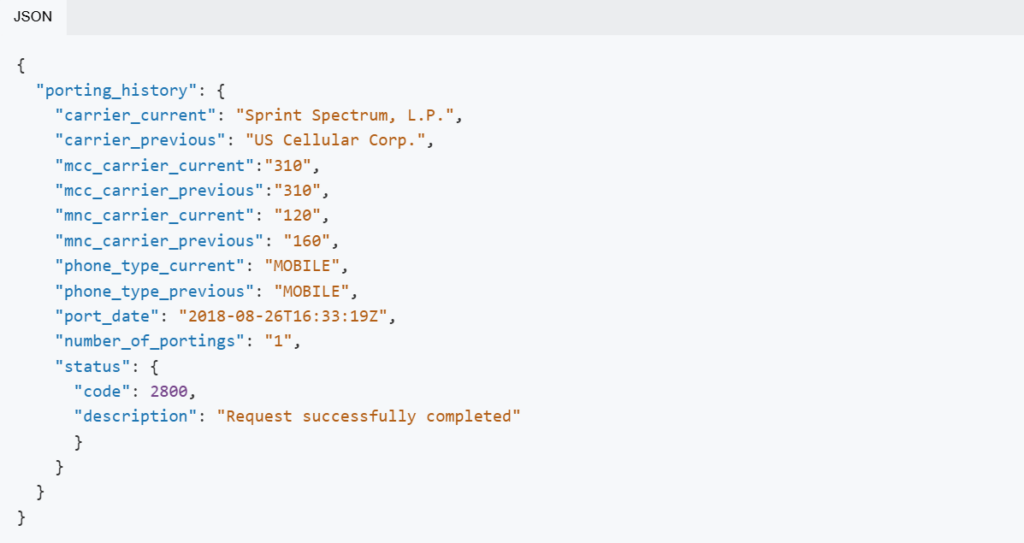
- Current and previous carrier name
- Current and previous MCC (mobile country code)
- Current and previous MNC (mobile network code)
- Current and previous phone type
- The date the number was ported
- The combination MCC and MNC uniquely identify a mobile network operator (carrier)
See how assessing the risk of port-out fraud with the Porting History identity attribute contributes to maintaining account integrity across the customer lifecycle.
How the Phone ID Porting History attribute works
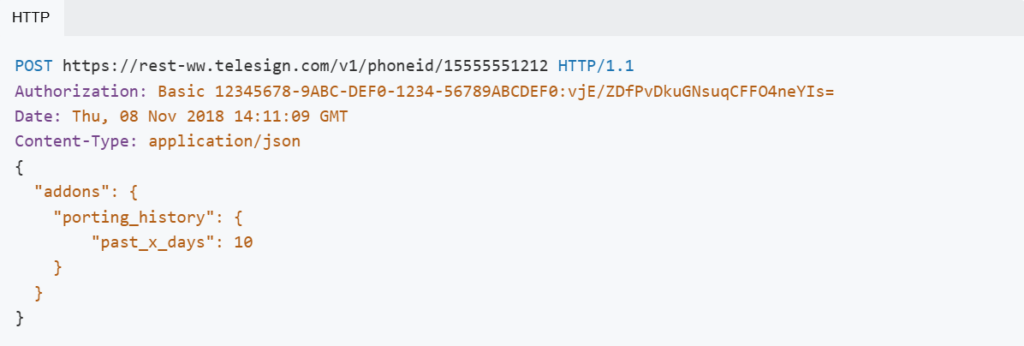
Example request
Example response
Try Phone ID with the Porting History attribute and access developer resources
Contact a Telesign expert to enable and try the Porting History Phone ID identity attribute for yourself.
Make sure to visit the Telesign Developer Center to learn about our APIs and quickly access documentation, GitHub repositories, and other technical resources.
Check out what else our APIs can do to help your business combat fraud and engage customers with our “There’s an API for that” blog series: