According to the 2024 Telesign Trust Index, data breaches accounted for 45% of reported fraud incidents in the U.S. and 46% globally, a number that’s increasing year-over-year as more brands are victimized.
While a data breach may be out of your company’s control, the consequences are not. If a fraudster uses breached data to gain access to one of your customer’s accounts, they can change account details, make unauthorized transactions, steal personal information, pollute the customer ecosystem with spam, and more. To protect your company and customers, it’s important to check for breached data status as part of your account integrity workflows.
In this API series blog article, you’ll learn how Telesign can provide real-time insights that flag phone numbers that have been involved in a recent data breach. This information can help you prevent synthetic identity fraud and account takeovers from fraudsters using stolen passwords and credentials.
Detect if an end user’s phone number was part of a recent data breach with phone number insights
Telesign Phone ID provides real-time information on the device type and contact information, along with other identity attributes.
Use the Phone ID Breached Data identity attribute to check if a phone number or any associated personal identifiable information (PII) was compromised in a recent data breach.
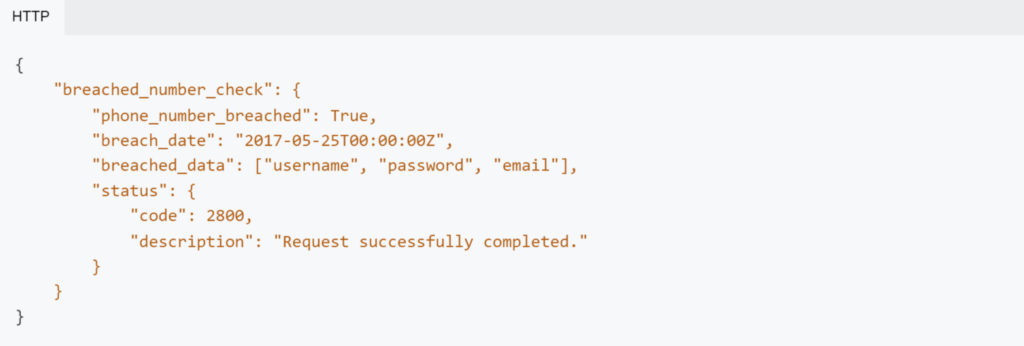
The Breached Data attribute provides a true/false response to indicate whether the phone number has been recently breached. For breached phone numbers, it provides the date of the data breach and lists the categories of other PII that were compromised.
How the Phone ID Breached Data attribute works
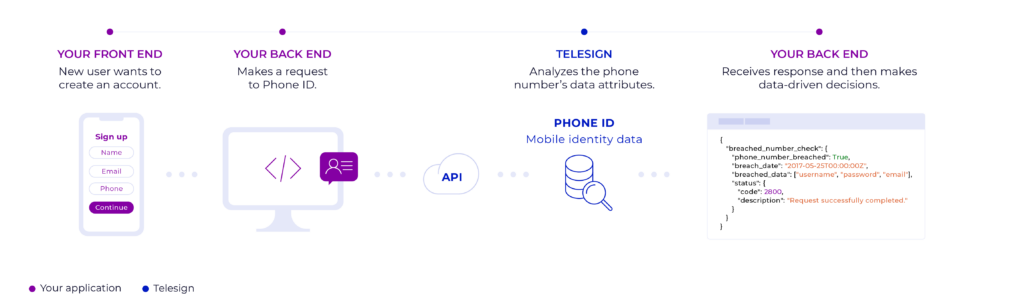
Example request
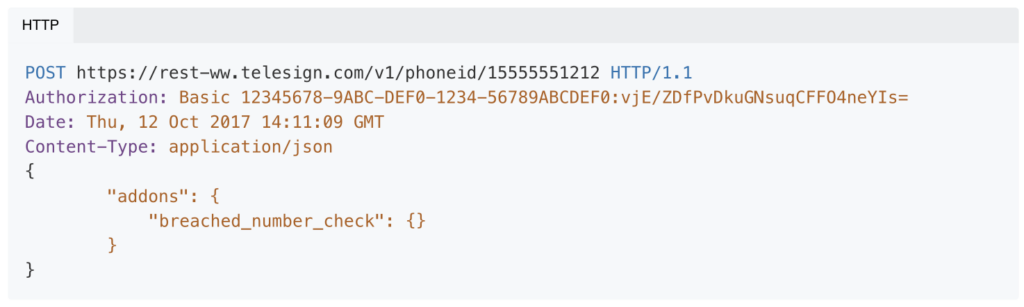
Example response when breach detected
Confirm identity to ensure account integrity
By checking a phone number’s breached data status as part of a Phone ID request, you can more thoroughly verify the legitimacy of an end user without adding friction to the user experience. After receiving a response indicating that a phone number was part of a recent data breach, confirm their identity using multifactor authentication (MFA). Our Verify API allows you to select from seven verification channels through a single integration and endpoint.
Try Phone ID with the Breached Data attribute and access developer resources
Contact a Telesign expert to enable and try the Breached Data Phone ID identity attribute for yourself.
Access the Breached Data attribute documentation for a more in depth look at examples and breached data types.
Make sure to visit the Telesign Developer Center to learn about our APIs and quickly access documentation, GitHub repositories, and other technical resources.
Check out what else our APIs can do to help your business combat fraud and engage customers with our “There’s an API for that” blog series: