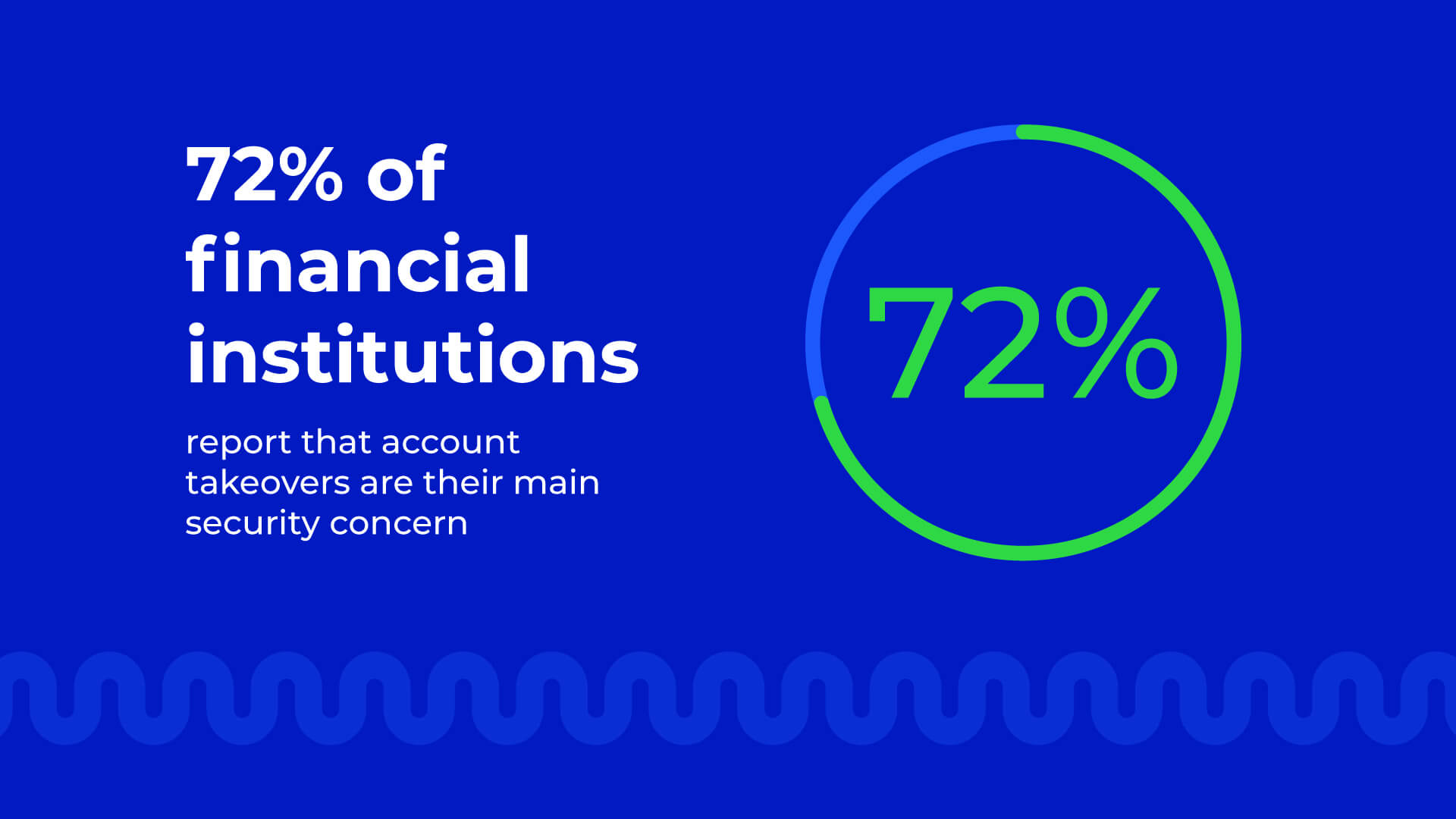
Account takeover (ATO) plagues digital businesses and cause significant financial and reputational losses. This persistent and often sophisticated tactic affects individuals and industries across demographics and industries. According to Consumer Affairs, 72% of financial institutions reporting that account takeovers are their primary security concern.
As more of our daily lives move online, ATO attempts are skyrocketing, rising a staggering 282% between 2019 and 2020. With the rise of ATO comes massive losses, affecting 24 million households at an average of $12,000 in losses, per Security.org’s annual ATO report.

What is an account takeover (ATO)?
Account takeover is a type of identity theft where account access is compromised, and someone who is not the legitimate owner of the account takes control of the account. An account takeover allows cybercriminals to modify important account settings, send phishing messages, make unauthorized withdrawals, steal sensitive data, access company accounts, and more.
What an ATO looks like
Despite the prevalence of account takeovers, most people don’t understand what to watch for or how it happens. An ATO begins like a tiny crack in a car’s windshield. Though the small break seems insignificant, it is compromising and will continue to grow. With ATO, all the fraudster needs is a tiny crack in the glass—a weak password, personal identifiers, public digital identity information and they’re in. From there, the cybercriminal’s foundation is laid, and they go to work using one account to take over another or building a digital identity that looks and behaves like a legitimate customer.
A successful account takeover is often executed in four steps:
Step 1: Compromise the user’s credentials
Most commonly, fraudsters target people who use weak or outdated passwords. People often use the same passwords for all their logins, and others don’t account for brute force attacks, making their passwords too simple and easily stolen. Studies have found that even today, many passwords are vulnerable to even the most basic hacking attempts, including human guesswork.
Step 2: Test if the accounts work
The next step in the account takeover is to test the stolen information. The fraudster takes the login details and other relevant details and uses them in the intended system to see if it’s valid, current, and provides access. They then poke around to test the level of access given.
Step 3: Bypass MFA
Armed with stolen credentials, the fraudster then bypasses any two-factor authentication associated with the account. This step varies based on the security system, and hackers use a barrage of techniques and tactics to bypass multifactor authentication (MFA), such as brute force attacks, social engineering, and more.
Step 4: Access higher-value accounts
Often, the final step in the account takeover is to up the ante by using the access gained to dig deeper into accounts connected to the stolen one. By doing this, fraudsters aim to break into an even higher-value account and obtain much more sensitive data and bigger payoffs.
Once the account is compromised, the bad actor often changes account settings, passwords, login names, security questions, and other key account credentials. Unfortunately for the victim – the actual account holder – they are now locked out of their account. Their attempts to regain access become much more difficult, as all the security prompts are now different and controlled by the fraudster.
Now that you’re familiar with what ATO is and how it happens, let’s look at who might be vulnerable to these attacks.
Who’s at risk of ATO?
With the continuing rise of ATO, it’s important to know who is most at risk so that you can build your defense accordingly.
In the past, fraudsters have targeted financial institutions, but now nearly any organization or individual with a user-facing login is susceptible to account takeovers. In terms of individuals, some groups fall victim to ATO much more often. According to Security.org’s recent digital safety studies, 75% of people aged 45 and above have experienced ATO, while only 69% of 18-29-year-olds did.

Here are some common underlying factors in people who are high risks for ATO:
- Use the same passwords on numerous accounts
- Neglect monitoring account activity regularly
- Use android operating systems
Of course, these factors don’t always lead to an ATO, but they certainly shouldn’t be ignored.
The trends are less clear when examining the types of organizations vulnerable to ATO. However, some departments need to be hyper-aware of potential ATO, as they’re more likely to be targeted. Departments with high-value information should prepare to be targeted more often. IT, finance, and HR teams are more frequently targets since they control employee data, security, or financial information.
We know which type of people and organizations cybercriminals target for account takeover now; let’s examine their methodology to gain entry to these accounts.
Current ATO tactics
Understanding the techniques used by fraudsters to conduct ATO is critical to building an effective prevention strategy. It would be easier to defend against if there were only one entry point, but unfortunately, cybercriminals use a wide range of tactics to gain access to an account.
Below are techniques fraudsters currently employ to gain access to victims’ accounts.
Phishing attacks
Phishing is when a bad actor sends deceptive digital messages to victims to trick them into providing sensitive information or infecting their systems with malware. There are several types of phishing attacks, all of which create the potential for ATO:
- Email phishing. Email phishing is the most common and usually the least sophisticated type of phishing attack. It is typically an email that attempts to impersonate a trusted company or person to trick the recipient into clicking a harmful link or sending personal information.
- Spear phishing. Spear phishing is tougher to deal with because the hacker sends victims a message that appears to be from a trusted source. For example, a cybercriminal may pose as a person’s boss or HR department in an email to get them to click a link or send sensitive information.
- Pop-up phishing. Pop-up phishing is simply fraudulent ads that randomly pop up when a victim visits a website. The most effective pop-up phishing occurs when hackers place these ads on legitimate websites, making them appear credible.
- Clone phishing. Clone phishing is where a fraudster sends an email that looks exactly like a legitimate email a victim has already received.
- SMS phishing (Smishing). SMS phishing, or smishing, is essentially the same thing as email phishing, only it’s done via smartphone text messages. The idea is to get recipients to open a link that steals information or installs malware.
SIM swaps
Since SMS MFA is a near-ubiquitous baseline method used to secure accounts, fraudsters have developed a method to breach the security they provide with SIM swaps. SIM swaps occur when a bad actor gathers personal information about a victim (often through phishing or purchased on the dark web) and then has that person’s wireless carrier change the victim’s phone number access to the scammer’s smartphone SIM card.
As a result, the fraudster’s phone now receives all calls and text messages sent to the victim’s device, allowing them to intercept the one-time-passcode (OTP) and bypass the authentication.
Types of hacking techniques
- Brute force attacks. A brute force attack is the most common hacking technique, as it is effective and can be automated. In a brute force attack, a hacker creates a code that tells a program to guess password combinations repeatedly until finding a working login.
- Botnet attacks. A botnet attack is when hackers use many compromised digital devices from various locations–making them less detectable/locatable–to conduct their fraud schemes. Botnet attacks allow attackers to gain control of multiple accounts simultaneously, thus increasing their ability to commit fraud undetected.
Social engineering attacks
Fraudsters combine publicly available information with manipulation tactics to commit a social engineering attack on a victim. They gather information from across the web, including social media accounts, to create fraudulent messages they send to victims. These messages pressure the victim to send sensitive data or information, often posing as their employer and asking them to address a seemingly urgent issue.
Potential impact of account takeover
ATO attacks continue to increase at an alarming rate as fraudsters expand their target base and refine their techniques for more significant payoffs. Although both individuals and companies are affected, businesses can be held liable when customers dispute fraudulent transactions, so the impact can be compounded and costly.
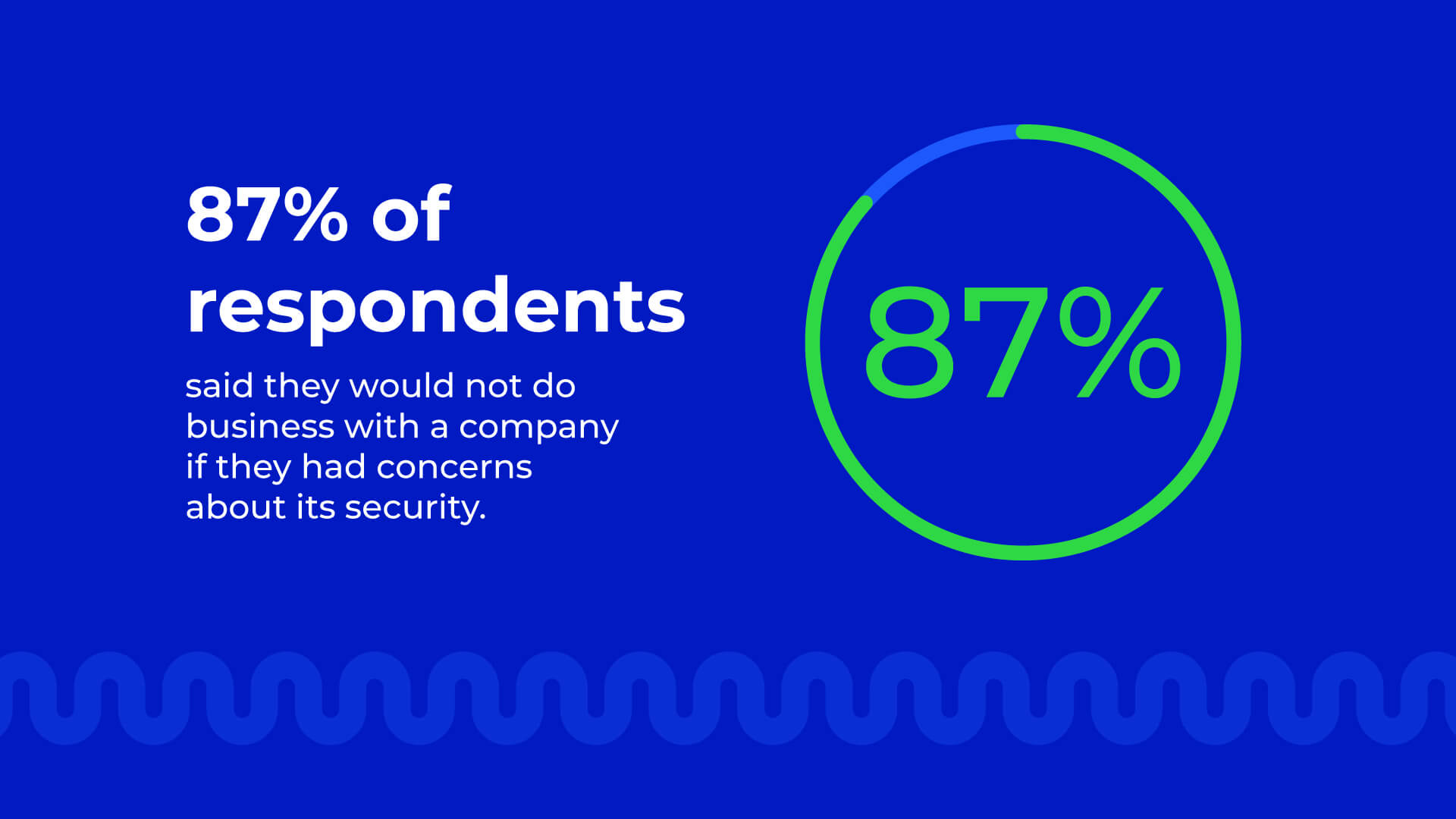
Building a solid relationship and gaining customer trust can make or break a business. Lost trust can be one of the most harmful results of account. According to a recent McKinsey report, 87% of respondents said they would not do business with a company if they had concerns about its security.
The following are the most common and harmful negative impacts resulting from ATO:
- Reputational harm. In today’s world of instant information and feedback, a brand’s reputation can be ruined with the click of a mouse. An ATO within a company can impact the entire brand name and send customers fleeing to competitors.
- Reduced customer engagement. Customers love to interact with businesses in which they have a strong relationship. If they feel their accounts or information are vulnerable with a company, they’re much less likely to interact and will look to take their business elsewhere.
- Unauthorized account access. Unauthorized access extends beyond the initial account takeover, as often the fraudster uses it as a steppingstone to infiltrate higher-level accounts to more significant – or even ongoing – financial or data fraud.
- Fraudulent transactions. Ultimately, most fraudsters conduct ATO schemes to steal money from individuals and businesses through fraudulent transactions, which is often the final step in the lengthy process.
ATO prevention tips
There are two different types of ATO prevention: direct prevention and detection. Below are a few tips to prevent ATO from happening or detect it when it’s in progress.
Prevention
- Limit login attempts. Login attempt limits make it much more difficult for a cybercriminal to spam attempts using numerous passwords.
- Enable MFA. Multifactor authentication adds another critical layer of protection to an account, requiring an account owner to provide a one-time passcode sent to a mobile device or email address to set up or access an account.
- Automate notifications for account changes. Create an automated system that sends users notifications whenever account changes happen. This helps keep awareness of changes and account activity high and shows your commitment to account security.
- Increase internal awareness. Keeping your internal administrators and team members educated with continued training on new trends and risky behaviors is critical in cutting down on ATO.
- Update your firewall. A firewall is an underrated tool in preventing ATOs, due to the way it handles tell-tale signs that a hacker is attempting a cybercrime. The best firewalls specifically recognize ATO patterns and techniques to help stop them.
Detection
In an ideal world, we could prevent all ATO from ever taking place. Unfortunately, there are too many moving parts within a company to avoid it from ever happening. When prevention fails, detection is the next layer of security measures.
Fraudsters don’t always use the same tactics and vectors, making detecting an ATO difficult. However, there are safeguards that individuals and companies can employ to detect and shut down an attack as it’s happening.
- Monitor vulnerable accounts. It’s not possible to closely monitor all accounts all the time, so pick your highest value accounts – like your mobile phone account, bank account, and primary email account – and monitor them closely.
- Check the validity of all email correspondence. It’s easy to turn your brain on autopilot when zipping through a bunch of new emails. However, this lack of focus is how phishing attacks succeed. Before committing to sending something out or clicking a link, be sure to check the sender’s authenticity.
- Be aware of account/profile information changes. One of the first things cybercriminals do after taking over an account is changing important information – including phone numbers, passwords, and email addresses – so only they can access the account.
- Monitor IP address changes. A single change in IP address from an unknown source usually is not cause for concern, but if login – or login attempts – are suddenly happening from inconsistent or unknown IP addresses, this can signal an ATO attempt is underway.
Protect your customers and your brand from ATO
Digital crime has grown so extensively that all companies and organizations, big and small, are vulnerable. Unfortunately, ATO is a trend that is heading in the wrong direction. Because of how damaging ATO can be to customer relations and brand image, it’s essential to minimize risks and employ a flexible, layered security stack that can stop fraud before it starts.

How Telesign can help
End-to-end account integrity is a dynamic, ongoing process. For more than 15 years, Telesign has helped the world’s most trusted companies keep their customers safe. As the industry leader in digital identity intelligence, Telesign harnesses billions of digital interactions, behavioral signals, and traffic patterns to continuously assess risk at key moments across your customers’ lifecycle. Proprietary machine learning adapts to unique business cases and delivers actionable insights codes so you can automate acceptance or rejection of logins, password reset requests, account updates, transaction verifications, and other high-risk interactions across your ecosystem. Telesign deploys a multilayer defense to protect against ATOs:
- Compile the right signals: Telesign’s PhoneID API taps into global identity datasets sourced from a combination of proprietary, signals, exclusive global partnerships, and client relationships. PhoneID makes available critical ATO risk signals – such as SIM-swap status, porting history, and more.
- Assess the risk: Telesign’s Intelligence is an adaptive machine learning model that assesses a user’s risk level in near-real time. Generate a risk score based on digital identity data (phone, email, and IP) that recommends whether to “allow” legitimate users and “block” or “flag” users who display fraudulent or risky traits.
- Verify Every Login: Telesign’s Verification API serves as the “possession” factor for multifactor authentication by delivering a one-time passcode (OTP) via SMS or voice to prove the user is in possession of their device.
Want further details about account takeover? Chat with us today.