Websites worldwide offer two-factor authentication (2FA), but a large number of consumers do not fully understand the technology, and therefore have not taken the steps to turn it on and protect their accounts. To help make the Internet a safer place for all, we decided to jump in and answer some frequently asked questions about 2FA.
Q: What exactly is two-factor authentication?
A: Two-factor authentication (2FA) is an additional layer of end-user account protection beyond a password. It significantly decreases the risk of account takeovers where a hacker accesses banking, shopping, social media or other online accounts by combining the password (something you know) with a second factor, like a one-time passcode or push notification sent to your mobile phone (something you have).
Q: Is this the same thing as two-step verification?
A: Yes. Websites refer to this security feature in several different ways: two-factor authentication (or 2FA), two-step verification (or 2-Step), multi-factor authentication and two-step authentication.
Q: Telesign and its Consumer Account Security Report reference a lack of confidence in passwords, but this implementation of 2FA utilizes a username and password. What makes passwords sufficient in this context?
A: The fact that a second factor of authentication is required significantly reduces the risk of compromise versus reliance upon a username and password alone.

Q: This report cites issues with passwords such as: they aren’t complex enough, they’re reused across multiple sites and they aren’t reset often enough. Don’t password managers solve these issues?
A: Password managers are great and they help guard against the risks that arise from people’s password habits. But they don’t protect against external threats to passwords. For instance, if a company’s database with passwords is hacked or if a personal computer is infected with malware that records keystrokes to steal account credentials, then the complexity and longevity of the password won’t help protect data. But 2FA will.
Q: What accounts should end-users protect?
A: It is an online security best practice to enable 2FA on all online accounts; including email providers, social networks, financial services, e-commerce sites, dating apps, gaming accounts, cloud computing and more.

Q: How do I enable it on these accounts?
A: Many of the world’s largest websites offer 2FA, but the instructions for turning it on vary from site to site. Telesign has put together an online resource to help guide you through the process, beginning with a list of sites that currently have the security feature available. Q: How does 2FA work?A: Two-factor authentication commonly works by asking for something you know (your password) in combination with something you have (your mobile phone) to confirm your identity across a variety of account activities–such as accessing your accounts from new devices, verifying transactions, or recovering your accounts. The process is simple. Once you enable 2FA on a site that offers it, a typical flow is as follows:
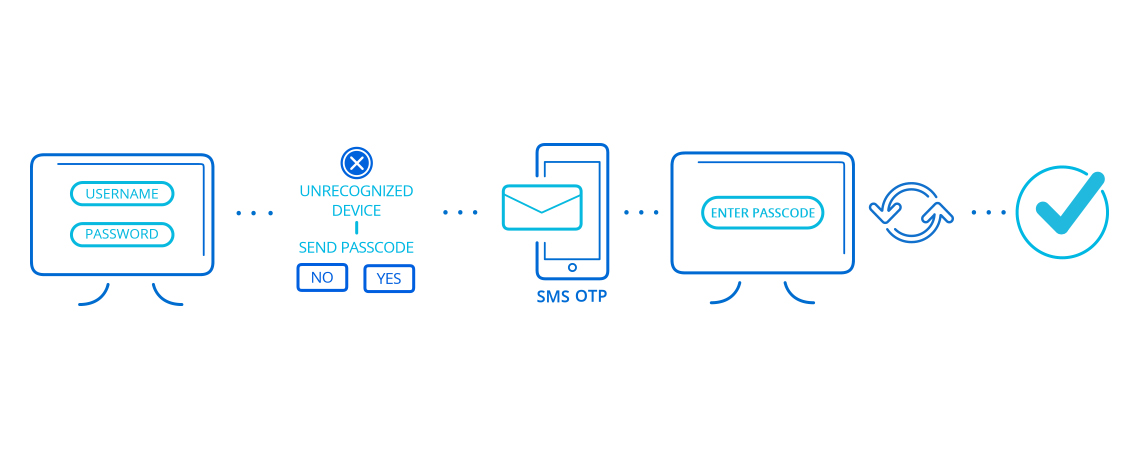
- You visit the site and enter your existing credentials (username and password) to access your account.
- If this is the first time you are accessing your account from a specific device, a “challenge” (a second factor) is needed to further verify that it is you, and not a fraudster.
- A code (a random set of numbers) is then sent via SMS, voice or push notification to the phone number that you used when you created your account. At the same time, you are shown a secondary login screen in your Web browser or on a mobile app from your mobile device with a prompt to enter the code.
- You simply enter the code that you received on the Web page or mobile app as prompted.
- Your account provider confirms that the code you entered is the same code that was sent to your phone and, if matched, you are verified.
- You are now able to access your account.
With 2FA enabled, a fraudster would have to have your username and password, and your mobile phone–at the same time–in order to access your account.
Q: What if I lose my phone?

A: If your phone is lost or stolen you should immediately contact your mobile phone carrier to lock access to the device. Additionally, to prevent unwanted access to your personal phone data and apps in the case where it is lost or stolen, it is always a best practice to utilize the lock feature in your phone’s settings. You should set your phone to lock and require a password for use of device when you are not actively using it. (General note on passwords: use different passwords across your accounts; use a combination of special characters, numbers and both upper and lowercase letters; avoid using passwords that include information that can be easily discovered online–like maiden names, high school mascots and phone numbers; do not create passwords that are so complicated that they need to be written down or that require a password reset on every login.)
Q: Do I really need 2FA?

A: Cybercrime is big business. In fact, account takeovers are expected to result in $8.3 billion in fraud losses by 2018*. Often, the cybercriminal behind these attack is using a stolen password to wreak havoc. Traditional password-based account security has become outdated. If you are using the same password on more than one site, downloading software from the Internet, clicking on links in email messages or even just signing in to your accounts from shared/public devices, you are putting yourself at risk for having your password stolen. And because many accounts simply require a username and password, anyone who steals that password can then log in as you. Having your password stolen and your account attacked is devastating. You could lose everything in it–emails, photos, sensitive information, all of your contacts… The list goes on. Fraudsters can lock you out of your account and then pretend to be you, sending messages to your contacts and posting as you for all to see. They can reset your passwords to other accounts. They can access your banking information. You can secure your account from compromise and verify high value transactions (such as accessing credit card details, transferring funds or making bill payments) by simply turning on 2FA.
Additional resources on 2FA:
*Source: Infiniti Research