When you think about the word identity, the first thing that pops into your head is likely security. Identities help us access our accounts in the real world, and our digital identities provide the credentials to access specific platforms in our digital lives. To write this blog, I had a one-time passcode sent to my phone to verify I was writing it. When I finish this article, I’ll post this to social media, where I will again prove myself with two-factor authentication credentials.
When you think of communication, you likely think engagement, alerts, notifications, or reminders. If I pull up my email right now, I’m reminded that my flight tomorrow is delayed, I have a credit card payment due, and my favorite cupcake company is giving 25% off for National Junk food Day. Hooray!

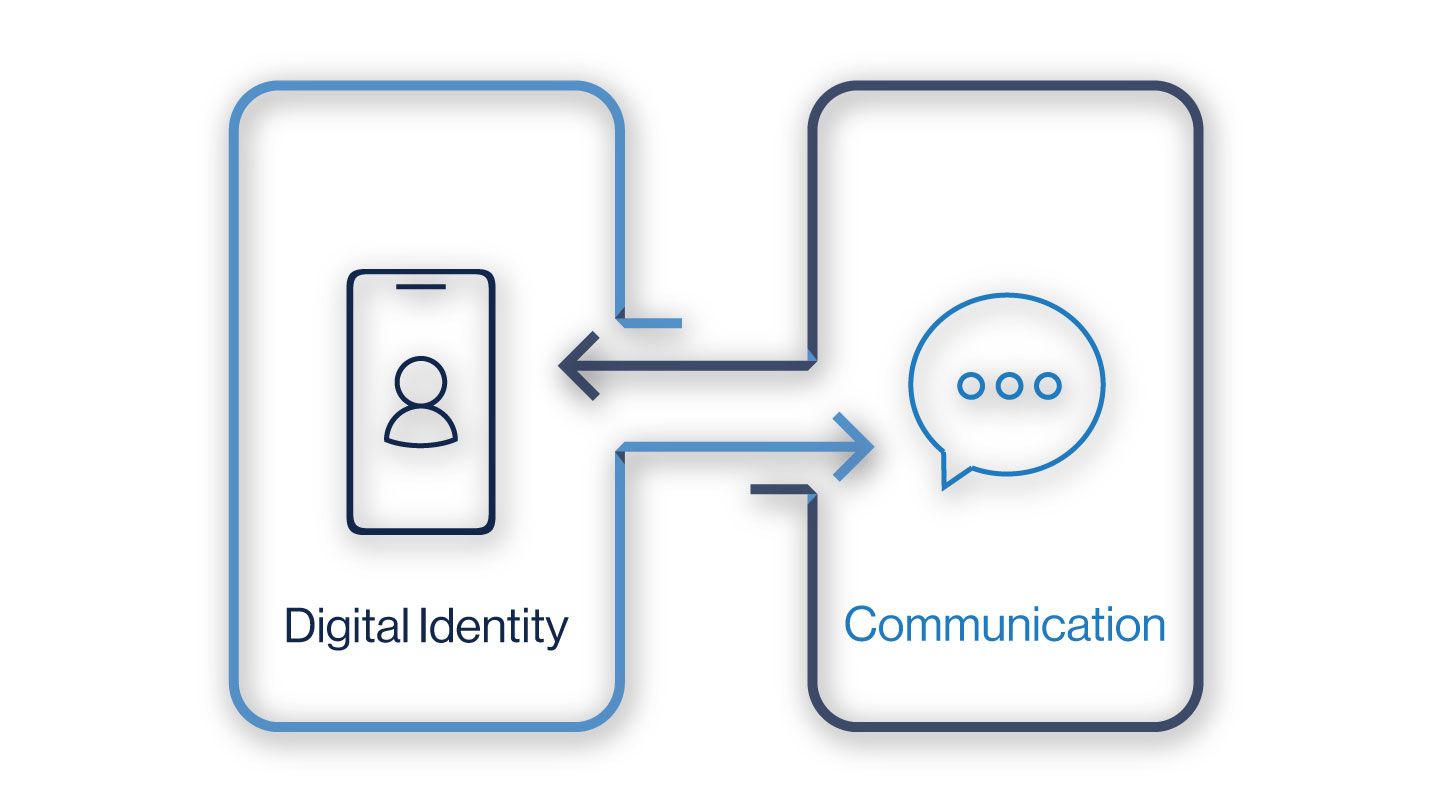
On its face, identity and notification are two rather different and distinct use cases, two that every online enterprise need but not necessarily use cases that are intricately connected. However, upon closer inspection, it will become apparent that you can’t have one without the other.
Consider the standard customer journey. Your platform asks for a number at registration for security purposes (verification) and communicative purposes (marketing) later. The usual way this works is when a person gives you a real phone number that is then linked to an account and begins to build a digital footprint about that user.
Scenario 1: Communication with no Digital Identity
Suppose I register to your platform with a burner phone or a free VoIP number I found online. Do you send an OTP without verifying what type of device I am using? This interaction scenario uses communication without binding it to digital identity. You’re sending an SMS but not further investigating what type of device is receiving the message. VoIP numbers, recently ported numbers, pre-paid, and dodgy SIM Cards are all types of numbers that add risk. Without running digital identity checks with that phone number, the verification process is effectively worthless. At best, you’re sending SMS to someone on a non-primary device; at worst, you’re helping register fraudsters and creating risk for your platform.
Scenario 2: Digital Identity with no Communication
Of course, there are two sides to this coin. If you are strictly using digital identity and merely running metadata checks on the phone number, I gave you, any data gathered by those checks is worthless. I could have given you my number, a VoIP number, a random number from the phone book. Some of those numbers will come back with no flags. But guess what most people know a person with a post-paid smartphone! Without linking that digital identity check to a real phone number in a person’s possession, you could be verifying fraud. Add a stolen social security number into the equation, and you may be in the early stages of developing a synthetic identity that damages your platform and destroys an innocent person’s credit for decades. Nice work!
Essentially a verification SMS without digital identity provides no value, and vice versa, one without the other is a fool’s errand. Why would you check what type of phone I claimed to have without making sure I had it? Why would you ask me if I had a phone number without confirming it’s not the type typically used for fraud?
Scenario 3: Digital Identity and Communication
It took us 600 words telling you what not to do, but here it is, the answer to the riddle. A smart platform with healthy security hygiene will ask for my phone number at registration. When they do this, they will first run a reputation score against that phone number and look at pieces of information that are high indicators of fraud. Furthermore, they will run specific API checks on contact information tied to the phone number, location, device, and porting history. By doing this (in milliseconds), the platform has a good idea of whether I am a good user or a fraudster.
Then they send a one-time passcode to the device to confirm possession. The user receives the one-time passcode and informs the platform that the phone hasn’t fallen into the wrong hands or fallen victim to a SIM Swap. It may sound cumbersome, but it’s the quickest and most effective way to validate good users. SMS has a 100% reach on mobile and a 98% open rate vs. 54% of email. The best news for you is that once you have your user validated, you can push them into your marketing queue, generate new revenue, and open new revenue streams (such as selling directly through SMS or RCS). This open communication line will allow you to send out important updates, critical information, or inform users of your junk food promotions (or whatever you’re in to.)
Telesign has been connecting and protecting online experiences for over 15 years. We support the largest web properties in the world and we’re prepared to help you. Contact Telesign now and for all of your security needs. As the pioneers of phone-based security, we are a one-stop-shop for all of your digital identity and programmable communications needs.